Information Assurance is Integral to the Mission
We at Haight Bey & Associates understand that Information Assurance and IT cybersecurity requirements are
integral to the successful completion of the mission. We are as equally adept at managing an IT system’s “in-theweeds”
technical configuration as we are at managing a comprehensive ATO portfolio. Let our cybersecurity experts
help you support your organization’s mission by securing your IT systems and managing your IT risk.
A Decade of IA Experience with USG Systems
Tactical
Weather-USAF Tactical Meteorological Observing System (TMOS)
Aerospace-Army Shadow & Grey Eagle UA

Enterprise
Healthcare-Centers for Medicare and Medicaid
C4ISR-Army PTDS/PSDS2
Cybersecurity is Risk Management
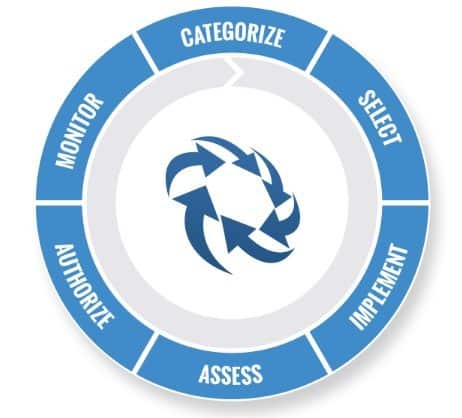
Cybersecurity entails the wise selection of mitigating actions–“controls”–to reduce risk to your organization posed by information, IT system assets, system users, and then assigning resources to implement and monitor those controls. Our cybersecurity experts are well-versed in the US Government RMF and its six cyclical steps: Aligning your organization’s IT system’s technical configuration, managerial policy, and operational processes to this framework is no small task. Haight Bey is here to help as we are experts in common execution tasks, including:
· Information categorization and classification
·Asset cataloging and configuration management
· Vulnerability scanning and compliance assurance
· Threat identification, tracking, and mitigation
·Assessment and Authorization of IT systems
Qualified, Experienced Experts
Haight Bey employees have over a decade of experience securing and monitoring US Government and DOD IT systems, including in classified and HIPAA environments. We’ve been involved in all aspects of system lifecycle security, from in-depth vulnerability scanning and remediation to Information Assurance portfolio management.
Our cybersecurity engineers hold degrees in the field, maintain top industry certifications, and attend regular advanced training to stay abreast of current industry state-of-the-art. We currently hold DoD 8570 IAM and IAT Level III certification.
100% Authority to Operate (ATO) Rate
Haight Bey is extremely proud of the fact that every system we have been entrusted to support has maintained its ATO, even through major system upgrades.
Vulnerability Management and Compliance
The RMF has strict requirements to comply with vulnerability management and configuration standards. We are well versed with DISA bulletins and standards such as IAVA and STIGs, and have executed ACAS since its inception. We’ve helped manage GRC tools such as eMass. We have the tools and techniques to help you manage the massive volume of compliance data.
Full IT Lifecycle Cybersecurity
Haight Bey has experience integrating cybersecurity into all phases of IT system lifecycle, from initial system concept and design, into operation, through major and minor system upgrades, culminating with system decommision. We’ve helped transition sytems from DIACAP to RMF, and have even assisted “onboarding” operational systems that had previously eluded IA oversight.
IA Staff Training
Let us help you train your internal staff to fill the critical IA management roles, such as Information System Security Officer (ISSO), or Information System Security Manager (ISSM). Members of Haight Bey have filled these roles in the past, and can provide the tools and sage advice to help your staff avoid pitfalls and successfully nuture your IT systems through the cybersecurity lifecycle.
ATO Package Development and Maintenance
Haight Bey has executed contracts to develop and maintain a full suite of policies, procedures, plans, and design documentation to support Assessment and Authorization of IT systems, in both unclassified and classified environments. We don’t treat this task as a “paper drill”; we pride ourselves in our attention to detail and creating relevant, meaningful, and actionable system security plans.
DFARS Compliant Internal Systems
The Haight Bey corporate IT network has been designed and is operated in accordance with DFARS clause 252.204-7012 “Safeguarding Covered Defense Information and Cyber Incident Reporting”. You don’t have to worry about us processing and storing your valuable information.